Disclaimer: I'm neither an experienced programmer nor proficient in reverse engineering, but I like at least to try to figure out how things work. Sometimes the solution is so easy, that even I manage to find it, still take this with a grain of salt.
I lately witnessed the setup of an Envertech EnverBridge ENB-202 which is kind of a classic Chinese IoT device. Buy it, plug it in, use some strange setup software, and it will report your PV statistics to a web portal. The setup involved downloading a PE32 Windows executable, with an UI that basically has two input boxes and a sent button. You've to input the serial number(s) of your inverter boxes and the ID of your EnverBridge. That made me interested in what this setup process really looks like.
The EnverBridge device itself has on one end a power plug, which is also used to
communicate with the inverter via some Powerline protocol, and a network plug with a
classic RJ45 end you plug into your network. If you power it up it will request an
IPv4 address via DHCP. That brings us to the first oddity, the MAC address is in the
BC:20:90 prefix which I could not find in the
IEEE lists.
Setting Up the SetID Software
You can download the Windows software in a
Zipfile, once you unpack
it you end up with a Nullsoft installer .exe. Since this is a PE32 executable we've to add
i386 as foreign architecture to install the
wine32 package.
dpkg --add-architecture i386
apt update
apt install wine32:i386
wget http://www.envertec.com/uploads/bigfiles/Set%20ID.zip
unzip Set\ ID.zip
wine Set\ ID.exe
The end result is an installation in ~/.wine/drive_c/Program Files/SetID which reveals
that this software is build with Qt5 according to the shipped dll's. The tool itself is
in udpCilentNow.exe, and looks like this:

The Network Communication
To my own surprise, the communication is straight forward. A single UDP paket is sent to the broadcast address (255.255.255.255) on port 8765.
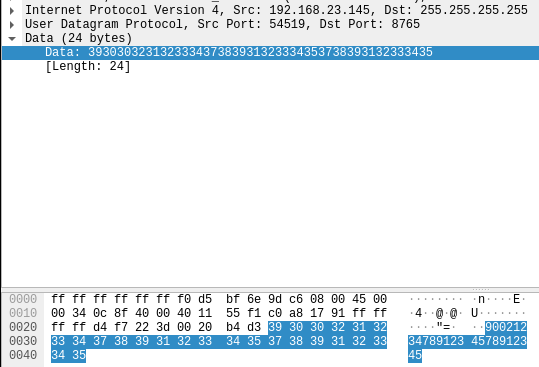
I expected some strange binary protocol, but the payload is just simple numbers. They're a combination of the serial numbers of the inverter and the ID of the Enverbridge device. One thing I'm not 100% sure about are the inverter serial numbers, there are two of them, but on the inverter I've seen the serial numbers are always the same. So the payload is assembled like this:
- ID of the EnverBridge
- char 9 to 16 of the inverter serial 1
- char 9 to 16 of the inverter serial 2
If you've more inverter the serials are just appended in the same way. Another strange thing
is that the software does close to no input validation, they only check that the inverter serials
start with CN and then just extract char 9 to 16.
The response from the EnverBridge is also a single UDP paket to the broadcast address on port 8764, with exactly the same content we've sent.
Writing a Replacement
My result is probably an insult for all proficient Python coders, but based on a bit of research and some cut&paste programming I could assemble a small script to replicate the function of the Windows binary. I guess the usefulness of this exercise was mostly my personal entertainment, though it might help some none Windows users to setup this device. Usage is also very simple:
./enverbridge.py -h
Usage: enverbridge.py [options] MIIDs
Options:
-h, --help show this help message and exit
-b BID, --bid=BID Serial Number of your EnverBridge
./enverbridge.py -b 90087654 CN19100912345678 CN19100912345679
This is basically 1:1 the behaviour of the Windows binary, though I tried to add a bit more validation than the original binary and some more error messages.